Today we’re going to take a quick dive into the security awareness around a practice that is called “phishing”.
This is a really important topic because believe or not, Phishing can be used against anyone, even someone who doesn’t even own a computer or smart phone.
What is Phishing?
For most people, hearing the word fishing conjures up thoughts of sitting on a dock or boat, tossing a line with some bait on it out into the open water, and see if anything bites. If you do get a fish hooked, you could end up with something you ignore and throw back, or you might get something big enough to feed a family. If you perfect your craft of catching fish by trying out different bait, changing locations, and even learning to lure in or “play with the line” to better emulate a live fish on your hook, you might get experienced enough to make this your full-time job and start selling your catch to others.
Now flip the story around and imagine you are a fish. Every time a bug hits the top of the water or something swims through your area of the ocean, you have to stop and wonder – is this legitimate food, or there a hook hidden in there somewhere?
This is how the term phishing, spelled ph-ish, came to be. In a security and privacy sense, the practice of phishing is when someone tries to use something that looks legitimate to get you to “bite” and offer up some of your personal information.
Phishing most commonly happens through a 2-step combination of email and websites, but can also used through a variety of ways:
- Text messages
- Phone calls
- Paper mail
- In-person talking
When we consider all the ways that can be used in phishing, we’re speaking of a form of social engineering.
How to Spot a Phish
Just like our example of a fisherman, someone who is trying to “phish” you will use some sort of bait, most commonly an email message. With this bait, they will try to get you to provide sensitive information, such as login credentials for your email or banking websites.
Being able to identify a phishing email can be easy, and it helps keep your online accounts secure.
1. Verify who the Message Was Addressed
Often you see phishing emails that are addressed to somebody generic such as “Hello client” or “Dear Customer”. When you stop and think about this for a moment, wouldn’t a company that you have done business with and you have an online account for their website already know your name?

2. Check the “From” Email Address, Not Just the Name
It is possible for an attacker to have access to or to fake the “From” email address (called “spoofing”), this extra level of detail usually isn’t found in phishing emails. Most often you will find that the Name portion of the “From” will look like a legitimate organization’s account, but the actual email address will be from a different source that doesn’t fully match. Any legitimate organization sending you emails should have their email addressed ending with a name that closely matches their actual business name.

3. Formatting and Spelling Errors
Any business you dealt with who is reputable and is concerned with the image they portray to customers will make sure they do proper editing and proofreading of their emails before sending.
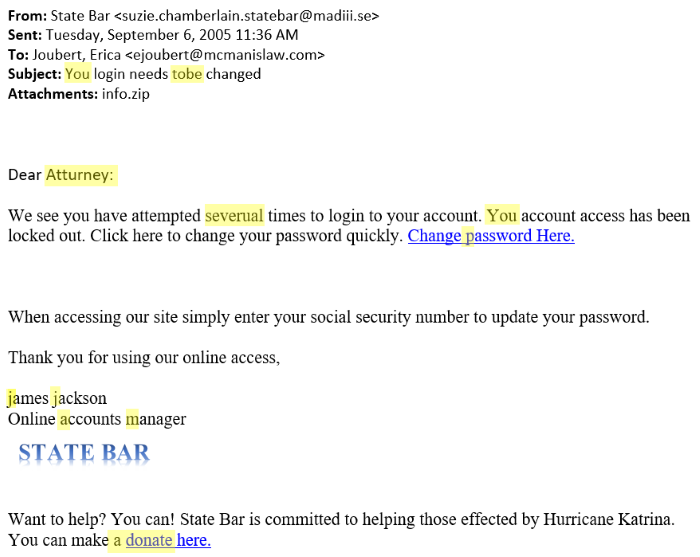
4. Overly Urgent Tone
Pay attention to the overall tone of the email. Often a phishing email will try to convey a sense of urgency to entice you to react in the moment. If you instead take time to pause and research the request, you may find the request was not real, which means the attacker lost their advantage.
When you find an email threatening you with fees, required verification, or account closure, don’t be afraid to investigate before jumping to action. Try manually logging in to your account on their website and see if another notice is shown to you on the screen that matches the email, or even call the organization and speak to someone on the phone – just be sure to visit their site for a valid Customer Service telephone number and do not use any numbers in the suspicious email.

5. Hover – Don’t Click – Any Links or Buttons
Many security experts rate this as the best method for detecting a phishing email, as it is the most difficult to fake.
Any time there is a link or button in the email prompting you to visit a site for login, verifying your credentials, or re-activating your account, you can check the URL of the website before actually visiting. Either in the bottom bar of your web browser or by hovering – not clicking – over the link, you should be able to see the full URL, not just only the text displayed in the email body.
If the email you received is trying to disguise as from your bank but the link URL goes to a website you haven’t seen before, then you know it’s the perfect time to classify this as a phishing email and delete it.

What If I Clicked?
Don’t Enter Any Information
If you did happen to click a link or button from a suspected phishing email, the best action you can do is nothing. Don’t enter any information into the website that opened, and delete the email. As long as you haven’t entered any information into the fake website, the attackers haven’t gotten any information from you.
Is it a Fake Website?
Just as looking for details in the email is important to detect a fake email, it is fairly easy for attackers to create a fake website to match their phishing emails. Begin by checking the website for similar spelling or formatting errors. The most telling sign of a phishing website is the URL shown in your browser’s address bar will not match what you expect based on the who the email is purporting to be from.

Change Your Password Immediately
If you think you might have previously visited a phishing website, you need to change your password to that site immediately.
To get started, visit the site with a saved bookmark or by using a well-known search engine such as Google, Bing, or Duck Duck Go. You want to avoid clicking any links in the suspicious email, or by typing a URL in the address bar of your browser. If you already visited a phishing site that has a name similar to the real site, your browser’s autocomplete feature may accidentally take you back to the phishing website again.
When changing your password, be sure practice good password guidelines and chose a password you have never used on any other site. This ensures that even if this specific password is ever stolen in the future, the attackers can only login to this single website, rather than use a single password to gain access to multiple accounts.
Stay Alert & Aware
One of the most common methods of theft of online personal accounts is because login credentials were accidentally provided through a phishing website. Always stay alert and aware of suspicious emails, and the links they contain, to make sure you keep your personal and sensitive information safe and secure while online!